Verifying a Face Certificate
How to determine the authenticity of a certificate
A Face Certificate is a standard x509v3 certificate and as such, its validity can be determined using conventional cryptographic tools such as OpenSSL:
openssl verify -CAfile root.pem -verbose face-cert.pemIn the above command, root.pem can be obtained by calling the /root-certificate end-point on the server.
As a standard cryptography construct, an x509 certificate can be verified using various libraries in many different languages:
Python - the
cryptographypackage support x509 verification. See here.NodeJS - pki.js provides functionality that should help in x509 verification.
C# - Useful functions can be found in the System.Security.Cryptography.X509Certificates namespace in .NET 8.
Java - This blog article covers a lot of gorund.
While the above list is by no means exhaustive, it should give you an idea of how you can verify certificates on your own server.
However, for the sake of convenience, we also provide an end-point for you to call to check the validity of a Face Certificate.
As before, on the Swagger Docs page authorize using the API Key you setup earlier.
Expand the /verify-face-certificate section and then click the Try it out button as shown below:
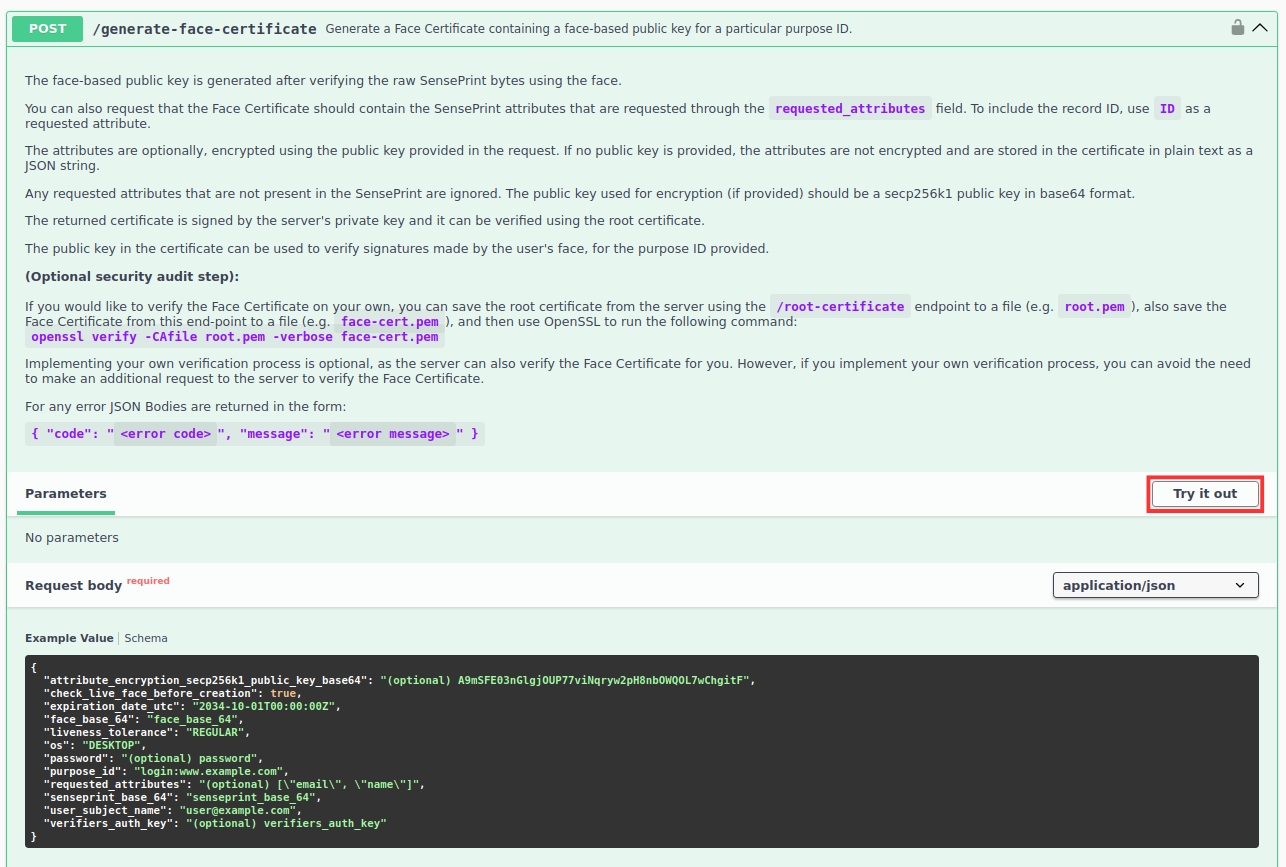
As before, after clicking the Try it out button, the following JSON text will become editable:
cert_pem - specifies the certificate to be verified (in PEM format)
secp256k1_private_key_base64 - when included, this key will be used to decrypt the eID attributes in a Face Certificate.
If the certificate includes encrypted attributes and this key is not specified, they will be returned as base64 encoded bytes which can later be decrypted offline using the ECIES algorithm (using your private key).
If the attributes were included without specifying a public key for their encryption, this parameter can be omitted and the attributes will be returned as a plain-text JSON string.
The process of generating keypairs for use with the API is described here.